Background
Network Attached Storage (NAS) is a key part of any enterprise today; they provide flexibility and an abstraction layer from an infrastructure perspective. In the heterogeneous enterprise, the easy part is the infrastructure piece; the hard part has to do with the diversity of platforms and the multiple file-sharing protocols in use. This post and a series of labs will illustrate how leveraging Active Directory, Centrify Zones, the Centrify agent for UNIX, Linux & Mac and the Centrify LDAP Proxy we can ensure consistency with multi-protocol CIFS/NFS shares and enhance operational efficiency.In previous posts, we have addressed how to to solve the consistency issue individually:
This posts uses a NetApp filer as an example(*). The concepts outlined here can be used on any NAS device that supports LDAP. We will assume that you understand that the fundamental problem is how to solve the issue of identity across multiple platforms and how we accomplish that with the Centrify Agent and Active Directory (I highly recommend that you read the previous links).
The Issues (or variations of it)
- We have a NAS device, we integrated it with AD and it works great as long as the user is performing file operations on Windows. However, we have to keep separate NFS shares. We also have to manage permissions in multiple groups (Windows or UNIX) and that takes a lot of effort.
Note, in my example with NetApp, the appliance does a great job at discovering LDAP servers:
netapp1> Sat Jul 5 11:26:52 EST [netapp1:auth.ldap.trace.LDAPConnection.statusMsg:info]: AUTH: TraceLDAPServer- AD LDAP server address discovery for CORP.CONTOSO.COM complete. 2 unique addresses found.
However, although it can resolve the AD portion, it is plain wrong about the Unix UID: - We have a multi-protocol share (CIFS/NFS), everything is great on Windows, when the user wants to access their files over NFS he has to call to have the file/folder ownership taken care of
- We are tired of having to resolve file ownership issues. Our organization is globally very diverse and each time we have a new visitor we spend significant amount of time helping them get access.
- We have a combination of Unix, Linux, Mac and Windows users and although we had it down in individual servers, when we moved to filers now we have all these new issues.
- I have a filer in my environment and we have Centrify as well, I know it can help but I don't now where to start.
Example of one of the issues
Let's look at an example. In my environment with a domain-joined Netapp the appliance does a great job at discovering LDAP servers (this happened once I searched for one of my users):
netapp1> Sat Jul 5 11:26:52 EST [netapp1:auth.ldap.trace.LDAPConnection.statusMsg:info]: AUTH: TraceLDAPServer- AD LDAP server address discovery for CORP.CONTOSO.COM complete. 2 unique addresses found.
netapp1> wcc -s george.constanza
(NT - UNIX) account name(s): (CORP\george.constanza - pcuser)
***************
UNIX uid = 65534
NT membership
CORP\george.constanza
CORP\UNIX-Model-Samba Users
CORP\UNIX-Model-All Users
CORP\UNIX-Model-dbaadmin
CORP\Domain Users
CORP\UNIX-Model-Sysadmins
CORP\UNIX-Model-webadmin
CORP\UNIX-Model-All UNIX Groups
BUILTIN\Users
User is also a member of Everyone, Network Users,
Authenticated Users
***************
This is great from a Windows perspective, however, look at the Unix UID (65534), when you look at the options, this means that the user is being assigned a "nobody" user from a UNIX perspective. We can further confirm this with this command:
netapp1> wcc -u george.constanza
no passwd entry for george.constanza
The way I have my system configured, although I can derive the user's identity leveraging the DCs, I can't see the user's Unix identity. It is stored in the zone. See the output from a centrified system:
george@ubu1:/etc/centrifydc/openldap$ adquery user george.constanza -A
unixname:george
uid:1149240406
gid:1149240406
gecos:George Constanza
home:/home/george
shell:/bin/bash
auditLevel:AuditIfPossible
isAlwaysPermitLogin:false
dn:CN=George Constanza,OU=Staff,DC=corp,DC=contoso,DC=com
samAccountName:george.constanza
displayName:George Constanza
sid:S-1-5-21-2180375406-786980114-1643973036-1110
userPrincipalName:george.constanza@corp.contoso.com
canonicalName:corp.contoso.com/Staff/George Constanza
passwordHash:x
accountExpires:Never
passwordExpires:Wed Aug 13 11:28:48 2014
passwordWillExpire:39
nextPasswordChange:Thu Jul 3 11:28:48 2014
lastPasswordChange:Wed Jul 2 11:28:48 2014
accountLocked:false
accountDisabled:false
zoneEnabled:true
unixGroups:dbaadmin,george,webadmin
memberOf:corp.contoso.com/UNIX/Provisioning/UNIX-Model-All UNIX Groups,corp.contoso.com/UNIX/Provisioning/UNIX-Model-All Users,corp.contoso.com/UNIX/RBAC/UNIX-Model-Samba Users,corp.contoso.com/UNIX/RBAC/UNIX-Model-Sysadmins,corp.contoso.com/UNIX/UNIX Groups/UNIX-Model-dbaadmin,corp.contoso.com/UNIX/UNIX Groups/UNIX-Model-webadmin,corp.contoso.com/Users/Domain Users
Our goal is to make sure that our filer (or application) gets the correct Identity information for the purposes of proper file/folder ownership, access and permissions.
Who's affected
As you can see, the variety of problems outlines have multiple constituents:
- Security needs to make sure that users have access to what they need and to comply with policies
- IT (business) need to make sure that users can do their jobs
- IT (operations) wants to be efficient and make sure that an army of people is not needed
- The End User just wants to get their job done
As with all Business Problems, we'll use the Plan, Do, Check, Adjust methodology.
Planning
As discussed in previous posts, the key to this issue is Identity. In this case, the NAS appliance needs to know not only the user's AD information, but the extended attributes (RFC2307) like unixname, UID, GID, Home, GECOS, Shell, etc., and unlike other approaches, Centrify stores this information in the zone. This makes the solution more flexible because an AD principal can have multiple Unix identities.
Note: If you've read this blog, you know that I've been very vocal about overrides (what enables multiple identities and roles). Every process needs to have constraints; constraints make solutions simpler. Having a normalized UNIX namespace is the goal and destination of any enterprise, even if Centrify allows you to put off this goal.
Identity and Access Planning
- Do the best you can to have a normalized namespace. Leverage Centrify's ability to assign users a unique UID by generating it from the AD SID (using Centrify or Apple's Scheme).
- Perform a migration if necessary (this post talks about strategies and Centrify tools for that purpose)
- Leverage the power of hierarchical zones: provision all identities at the top-most zone. This will ensure that all pertinent systems will know the user's identities.
- Continue to enforce the least-access principle: Use the "listed" role to make users known to the systems (e.g. the LDAP proxies) and ensure that they can't sign-in to the systems.
Planning your LDAP Proxies
The Centrify LDAP proxy leverages the Centrify client (adclient) to present AD information to clientless devices or programs. The benefits of leveraging the proxy are:
- It flattens AD for the application: depending on the enterprise, AD can be complex. There may be multiple forests, child domains, one-way, two-way trusts, etc.
- It leverages the agent's built-in capabilities: optimal DC selection, site-awareness and offline cache.
Plan for high-availability: the NAS (or application) is going to require redundancy, plan to deploy and configure multiple proxies.
Plan for confidentiality: make sure that only authenticated connections over secure transports (TLS, SSL, etc) in case your appliance or application does not do it natively.
Plan for high-performance: As always, have NSCD on the Centrified system, and plan for co-location near the appliance, application and be close to Global Catalog servers in complex environments.
Plan for your file-sharing use case
This section varies based on what you want to accomplish. Planning for home directories is not the same as planning for a workgroup share.
Implement (Do)
- Unix-enable all your relevant users (you don't need to Unix-enable users that won't ever access via NFS). You can do this manually, with ZPA or with your own IdM solution.
- Assign roles as required: keep the least-access principle intact by leveraging the "listed" role.
- Install the LDAP Proxy(es):
- Copy the Centrify LDAP proxy binaries to the platfrom.
e.g. for Ubuntu on 2014: centrifydc-ldapproxy-5.1.3-deb5-x86_64.deb - Log in and install the package
e.g. dpkg - i centrifydc-ldapproxy-5.1.3-deb5-x86_64.deb
The LDAP proxy binary is on /usr/share/centrifydc/libexec
The config files and schemas are in /etc/centrifydc/openldap
The LDAP utilities (like ldapsearch) are on /usr/share/centrifydc/bin - Modify the RFC 2307 map
- Edit the /etc/centrifydc/openldap/rfc2307.map file
- Add the following line (for NetApp compatibility):
# Added for NetApp
posixAccount.userPassword: _userPassword - For testing only, start slapd manually:
dzdo /usr/share/centrifydc/libexec/slapd -f /etc/centrifydc/openldap/ldapproxy.slapd.conf -h ldap://ubu1.corp.contoso.com - Check that the proxy is running
$ ps -ef | grep slapd
root 23192 1 0 Jul04 ? 00:00:00 ./slapd -f /etc/centrifydc/openldap/ldapproxy.slapd.conf -h ldap://ubu1.corp.contoso.com - Verify that the proxy is responding to queries (e.g. check the Administrator account)
$ /usr/share/centrifydc/bin/ldapsearch -h ubu1.corp.contoso.com-x -b "dc=corp,dc=contoso,dc=com" "(cn=Administrator)"
# extended LDIF
#
# LDAPv3
# base <dc=corp,dc=contoso,dc=com> with scope sub
# filter: (cn=Administrator)
# requesting: ALL
# with pagedResults control: size=100
## Administrator, Users, corp.contoso.comdn: cn=Administrator,cn=Users,dc=corp,dc=contoso,dc=comaccountExpires: 0
(output truncated***) - Configure your NAS appliance (e.g. on NetApp Ontap v 8.1.2)
- Housekeeping: Make sure that the name of the appliance is resolvable (add an A record for it) and that all Centrified systems, Windows Systems can resolve it. The NetApp system should resolve all systems as well. E.g.
netapp1> ping ubu1
ubu1.corp.contoso.com is alive
netapp1> options dns
dns.cache.enable on
dns.domainname corp.contoso.com
dns.enable on
dns.update.enable off
dns.update.ttl 24h - Housekeeping: Make sure that CIFS and NFS are licensed, enabled and the NetApp filer is joined to the domain. (use the license command, the cifs setup command )
- Verify that there's a computer object for the netapp device and that you can (as a Domain Admin) connect to it via Computer Management. E.g. using ldapsearch:
george@ubu1:/etc/centrifydc/openldap$ /usr/share/centrifydc/bin/ldapsearch -h
ubu1.corp.contoso.com -x -b "dc=corp,dc=contoso,dc=com" "(cn=NETAPP1)"
<truncated>
# NETAPP1, Appliances, corp.contoso.com
dn: cn=NETAPP1,ou=Appliances,dc=corp,dc=contoso,dc=com
<truncated> - Optional: Make sure that Domain Administrators are not mapped to root the NetApp filer:
netapp1> options wafl.nt_admin_priv_map_to_root off - Configure NetApp to use the LDAP Proxy (Example corp.contoso.com; ubu1)
- Set up the LDAP base container
netapp1> options ldap.base dc=corp,dc=contoso,dc=com - Set up the LDAP server(s) to be used by the NetApp appliance
netapp1> options ldap.servers ubu1.corp.contoso.com - Set up the name of the Active Directory Domain
netapp1> options ldap.ADdomain corp.contoso.com - Map the userPassword attribute to avoid null results
netapp1> options ldap.nssmap.attribute.userPassword cn - Enable LDAP
netapp1> options ldap.enable on - Modify the /etc/nsswitch.conf to make LDAP the first source for user, group and shadow entries.
netapp1> wrfile /etc/nsswitch.conf
hosts: files dns
passwd: ldap files
group: ldap files
netgroup: files nis
shadow: files nis - Verify the results
- Query and note the UID from Windows
wcc -s jerry.seinfeld - Query and note the UID from UNIX
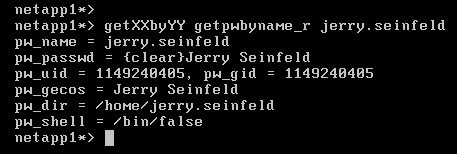
wcc -u jerry.seinfeld - Advanced query using NSS
priv set diag
getXXbyYY getpwbyname_r jerry.seinfeld
Compare the results with the zone information. At this point it should match the UNIX identity on Access Manager
Check the Results
To verify the results, use a multi-protocol (CIFS/NFS) share and make sure that the identity information is consistent.- From a Windows system in the target domain, map or browse to the share via CIFS. Create a file.
- From a Unix/Linux or Mac system, mount the share as an NFS mount and issue the ls -la and ls -lan. Compare the results from before.
Adjustments to the Implementation
Adjustments are based on your existing environment, however, based on ours here are some key modifications:
- There's only one LDAP proxy, we need several for high-availability
- The LDAP Proxy is accepting anonymous connections, we need to make sure that only authenticated connections are accepted.
- Ideally we would use Secure LDAP or implement TLS or IPSec for additional confidentiality controls.
- Operations needs to monitor the health and status of the LDAP Proxies
Lab Videos
What you'll need to follow along:
- Active Directory
- Centrify Standard Edition
- A Centrify zone
- Client for Unix, Linux or Mac
- Centrify's LDAP Proxy
- A Multi-protocol filer (we'll use NetApp's ONTAP Simulator)
Installing, Configuring and Testing the Centrify LDAP Proxy
Configuring the NetApp appliance to use the Centrify LDAP Proxy
Verifying the NetApp CIFS/NFS share provides consistent identities

No comments:
Post a Comment