Background
Digital Certificates have an important place in a properly managed enterprise. From an infrastructure perspective, they can enhance authentication and provide encryption for Ethernet and Wifi Networks.Centrify for Mac OS X has built-in capabilities to enable 802.1x authentication leveraging Group Policy but it does require that the computer has a digital certificate.
PKI Disclaimer: As in all PKI-related posts and videos, I make the caveat that Public Key Infrastructure is no joke. There are policy, people, process, security and technology implications to your enterprise, so all PKI deployments need to provide a high-level of assurance. You may have landed here due to a google search or reference, feel free to use these posts for testing purposes, but again, when it comes to PKI, any production deployment should conform to best practices.
 |
| Centrify uses GPOs to configure computer or user-based 802.1x settings on the Mac OS X platform |
Configuring Computer AutoEnrollment for Mac OS X
The Centrify adclient is capable of leveraging Windows certificate auto enrollment with the Microsoft CA. The basic steps are:On the AD side (with a Domain or Cert Admin)
- Configure the certificate template based on your needs (using the Certificate Templates MMC)
- Subject (typically common name based on the User Principal Name)
- Security (set it to an AD group containing your Mac Systems and check to Enroll and AutoEnroll)
- Extensions (add what you need)
If using it for 802.1x - usage should be Client and Server Authentication. - Configure your CA to issue Certificates based on that template (using the Certificate Authority MMC)
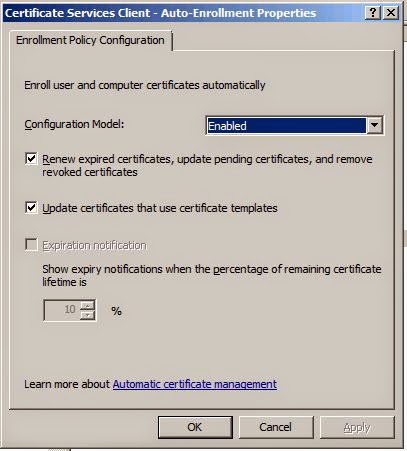
- Modify your GPO to enable the PKI policies for auto-enrollment
Enabling the Computer Configuration > Windows Settings > Security Settings > Public Key Policies > "Certificate Services Client - Auto-Enrollment Settings" GPO
On the Mac (domain-joined)
- Flush the cache with adflush (or wait the cache flush interval) [sudo adflush]
- Refresh the group policies (with adgpupdate) or wait for the GP refresh interval
- Verify the Certificates on the Keychain Access app.

No comments:
Post a Comment