Background
Maintenance activities are part of any IT professional's basic tasks, and Centrify provides many tools for administrators to facilitate proper maintenance and cleanup of Centrify-related objects in Active Directory; as a matter of fact, it's expected that any customer of Active Directory maintains basic "etiquette" like:- alignment with established naming conventions: for example; in the context of a computer role. What's more descriptive for the AD group? "webservers" or "centrify-unix-global-cr-webservers"
The first one could be any web servers, including IIS; however, the second one follows a naming convention that goes from the general to the specific. We know it's related to Centrify due to the name, used for UNIX-like platforms, in the global zone, it's a computer role (cr) and the name is web servers. - do not use software that makes direct LDAP connections to domain controllers, leverage software that is aware of the AD topology defined in Sites and Services
This one may not be very clear to everyone. Unfortunately many IT Pros equate AD to LDAP and that could not be further from the truth. Active Directory maintains a topology and uses DNS to ensure high-availability; sites and services aware programs (like the Centrify base and audit agents) will switch and perform telemetry calculations. The issue with straight LDAP binds is that depending on the application, it may spawn multiple threads of TCP connections that don't act like web connections, these are persistent connections that use CPU and memory. It is not fun when you get a call with the "j'accuse" an application for killing a specific domain controller. When in doubt, use the Centrify LDAP proxy instead of connecting directly to an AD domain controller. - cleanup after yourself: when objects are not used, delete them
This may come as no surprise, but looking at many deployments, I don't see very good hygiene. Perhaps it's important to understand how the internal workings on how Active Directory stores data. Active Directory uses the extensive storage engine (ESE, legacy name "Jet") - ESE data only grows in size in the operating system; however the engine is very mature and resilient; it will perform online defragmentation; in addition, replication only happens with deltas. If you cleanup after yourself, although the size of the file (ntds.dit) will continue to grow, internally it may be able to reclaim space. - communicate and work together with your AD team
This one may be a shock to those who are still stuck in the early 2000s. When you implement a cross-functional solution like Centrify Server Suite that combines Security Capability (Access Control) with Directory Services (Windows) and Open Systems (UNIX, Linux, Mac); there's an underlying expectation that you will work together as a team. This means understanding that there's a dependency on a utility service (Active Directory) that both users and critical apps are relying on. Network folks also have a role here; new subnets have to be communicated to the AD team for proper sites and services topology; AD teams MUST consider UNIX, Linux and Mac teams when major changes happen like Domain/Forest functional levels change or when new type of DCs are added (e.g. Windows 2012 R2+). Security folks also need to understand that instead of having things done for them (e.g. those dreadful reports); they can work to have those created for them on SQL Server or using automated tools like PowerShell. The game here is to provide results for the business while maintaining a proper security posture, not the early 2000's immature battle of "My Linux does not go near Windows"
Common Hygiene Issues
- Orphaned Objects:
This one is the most common in my opinion. An orphaned object is created when the parent of a child object is deleted and the child is left behind. Some apps (like ADUC) are smart enough to delete any child objects if the proper plugins are installed; e.g. Exchange, Centrify. Some examples include: - Deleting a user object without deleting any UNIX profiles
- Leaving the domain with adleave and teh --force option (offline leave) and not cleaning up the computer object in AD. The proper way is to perform an adleave with connectivity with the --remove option.
- Deleting zones without proper cleanup: many customer are phasing out classic zones and not properly decommissioning them.
- Unused Objects: Some examples include: empty roles, unused roles, etc.
- Improper permissions: For example, a computer that can't update it's OS information.
The Analyze Wizard Tool
Centrify's Access Manager includes a Utility called the Analyze Wizard. This tool allows for the identification and correction of common issues.
You can launch the Analyze Wizard from the left pane of Access Manager by right-clicking the DirectManage Access Manager [domain controller] node and clicking "Analyze"
You can launch the Analyze Wizard from the left pane of Access Manager by right-clicking the DirectManage Access Manager [domain controller] node and clicking "Analyze"
Once launched, you can select the checks to be performed.
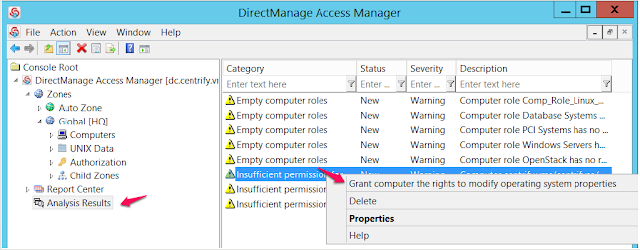
Once you run the Analyze tool, it will present its results in a brand new node in the left pane of Access Manager.
You can browse to the issues, as you right click them it will provide you an automated way to resolve the issues provided that you have the proper rights in Active Directory.



No comments:
Post a Comment